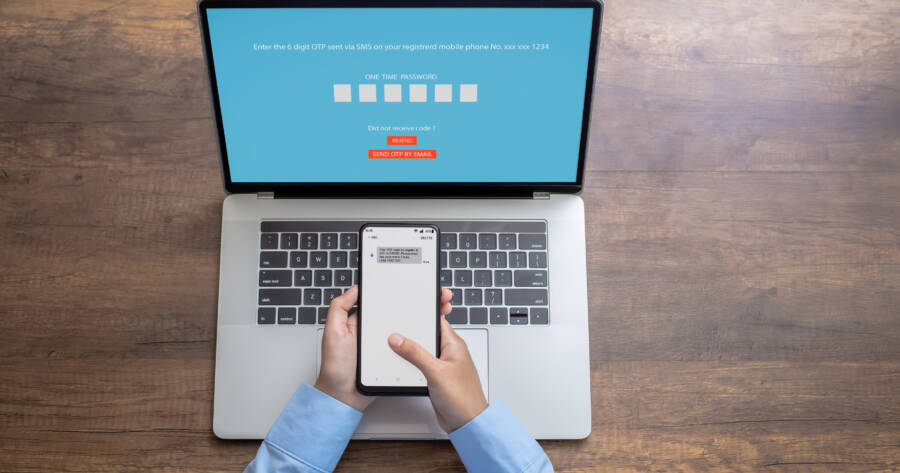
- Two factor authentication – which may engage two of five different factors – requires a user to offer at least two authentication methods before they’re granted access to a website or network.
- While it’s just becoming standard on many concur websites, it’s been around since the mid 80s.
- 2FA is the bare minimum a company should be doing to protect its data and it’s imperative that consumers opt for websites that offer this form of security.
Two factor authentication (2FA) is a security protocol that requires users to engage with two different authentication methods when attempting to access resources on a computer network, in addition to the standard practice of entering a username and a password.
 Shutterstock
ShutterstockHistory of 2FA
2FA is commonly thought to have emerged during the 2010s, but in actual fact, the technology can trace its roots back to the late-20th century.
In 1986, the Massachusetts-based cybersecurity company, RSA, programmed an LCD on a small key fob to display a series of numbers, which had to be entered alongside a user’s password before they were granted access to the internal IT network. In the following years, enterprise-level organizations adopted the practice of requiring multiple authentication factors to control access to virtual and physical assets.
It wasn’t until 2010 – well into the digital era – that 2FA was adopted as standard. In January of that year, Google announced that due to repeated attacks on the Gmail accounts of a number of human rights activists in China, it had been forced to suspend its Chinese operation and implement 2FA for all Google Business accounts. The process was extended to all Google users as standard in 2021.
Following Google’s lead, major software companies, financial institutions and government organizations started to cast aside traditional methods of authentication, and implement a more secure alternative in the form of 2FA.
Since then, 2FA has undergone multiple iterations that incorporate biometric information, and an advanced version called ‘multi-factor authentication’ (MFA) that requires any number of verification methods, not limited to two.
 Shutterstock
ShutterstockHow Does 2FA Work?
When users attempt to log in to a cloud-based or on-premise network – either as part of their job, or when using consumer software such as banking apps and ecommerce platforms – 2FA requires them to verify two pieces of information, also known as ‘factors’, from the below categories:
- ‘Knowledge’ factor – something the user knows, most commonly a password or PIN number. Knowledge factors are also known as ‘secrets’.
- ‘Possession’ factor – something the user owns or has access to, such as a mobile phone authenticator app, a physical device (ID card, key fob) or a token.
- ‘Biometric’ factor – this is anything that can identify the user as being themselves through biological information such as fingerprints, speech patterns or iris patterns.
- Timed factor – restricts login attempts to a specified time period.
- ‘Location’ factor – where the authentication attempt originated from, verified by methods such as IP addresses or GPS information obtained from a laptop or mobile phone.
IT administrators can specify which of the above factors are required, prior to a user being granted access to a network. In general, most 2FA platforms ask for the first three – location and timed factors are usually reserved for internal IT networks and remote working policies.
 Shutterstock
Shutterstock2FA vs. Standalone Passwords
2FA is deployed with the sole purpose of preventing unauthorized access to a computer or network system. If your organization is content with relying solely on a username and password to authenticate users, you need to revaluate your security procedures. The logistic considerations are insignificant next to the prospect of a data breach. Companies who fail to enact robust 2FA authentication procedures run the risk of exposing their IT infrastructure and financial assets to cyber criminals looking to exploit lax security protocols.
Passwords, when used in isolation, are markedly less secure than requiring several methods of authentication. Usernames are relatively easy to guess, and follow a standard ‘firstname.surname’ or email address format. Passwords should, in theory, be a lot harder to crack, but in practice there are several methods that cybercriminals use to take advantage of unsecured login information.
Let’s look at some common issues, and how 2FA helps to minimize the risk of intrusion.
 Shutterstock
ShutterstockPassword Complexity
Passwords should be of an appropriate length (usually a minimum of 8 characters) and contain a complex string of alphanumeric information, including uppercase and lowercase letters, and special characters.
Users often forego standard practice and use the same password across multiple private and public platforms. This can cause data breaches to escalate from relatively minor intrusions involving personal email accounts, to large scale instances of corporate theft, using the same password information across multiple platforms.
2FA prevents this by attaching each account to several factors that require additional information, over and above the compromised password.
 Shutterstock
ShutterstockSocial Engineering
Hackers use all manner of methods to gain access to a user’s password, including ‘social engineering’, whereby users are contacted directly by cyber criminals posing as someone else (such as a manager at work or a member of a law enforcement agency), and fooled into handing over passwords and sensitive information.
Social engineering methods are becoming increasingly sophisticated, and often include email spoofing – a trick used to mimic the email address of a trusted source. By requiring biometric and locational factors at the point of login, 2FA acts as a failsafe in the event of a person unsuspectingly providing information to someone looking to exploit unsecured systems.
 Shutterstock
ShutterstockPassword Cracking
Passwords are essentially small pieces of data, and as such can be disassembled or accessed just like any other string of data, albeit in a much more complicated way. Hackers use highly specialized, sophisticated software to gain direct access to a user’s password using one of three methods:
Brute-force attacks
Dictionary attacks
Rainbow attacks
2FA mitigates the threat of all three by ensuring that the compromised password is not the only piece of data required to access a network.
 Shutterstock
ShutterstockPoor Off-Boarding Procedures
When employees leave your organization, it is essential that they do not retain access to your IT assets. All too often, companies fail to change a former employee’s password, which can lead to all manner of problems, not limited to IP theft, data breaches and reputational damage.
By requiring multiple forms of verification, such as linking a user’s account to an official authentication app (‘possession’ factor), firms are ensuring that disgruntled employees are provided with the fewest number of opportunities to cause havoc.
 Shutterstock
ShutterstockHigh-Profile Hacks
2FA plays an integral role in securing personal and commercial information in the era of high-profile corporate data breaches. In an IBM report in 2021, data breach costs rose from $3.86 million in 2020 to $4.4 million in 2021 – the highest these costs have been for nearly 20 years.
When a user logs into an online service, the information they enter – everything from usernames and passwords to personal information – is stored by the website. User’s have no control over how this information is kept secure by third party companies and place their trust in multinational organizations to enact robust security protocols to keep it out of the hands of opportunistic criminals.
If compromised, this data can be used by hackers to access accounts across a variety of different platforms. Using 2FA gives you the best chance of avoiding any collateral damage by requiring multiple verification steps on an account-by-account basis.
 Shutterstock
Shutterstock2021 LinkedIn Data Breach
It’s not all about password security. In 2021, a hacker by the name of ‘God User’ exploited a security vulnerability in the professional networking site, LinkedIn, and stole the personal information of 92% of its user base (approximately 700 million users) in what is widely regarded as one of the biggest website hacks of all time.
While the breach did not include passwords, it contained the following information:
- Email addresses
- Phone numbers
- Geolocation records
- Genders
- Social media details
All this information can be used to guess or reset passwords across various different online platforms. Unless those platforms utilize 2FA to secure accounts, the potential for additional breaches is enormous.
 Shutterstock
ShutterstockAn Essential Tool for the Digital Age
Enacting 2FA is the minimum that organizations can do to secure their data and protect the identity of their employees and customers. It is no longer sufficient to rely on usernames and passwords alone.
If your organization doesn’t already use 2FA, consult with your teams immediately on how best to implement it. The technology has been around for over a decade and IT staff are broadly familiar with its requirements.
If you’re a private individual, make sure that every service you use offers 2FA as standard. If it doesn’t, use another company who is serious about cybersecurity. Don’t risk becoming another statistic.